Is Anyone Watching My Security Cameras?
Your new security system was installed a few weeks ago and seemed to be working great. You spared no expense and got all the bells and whistles - door alarms, window alarms, cameras, control apps, and “24-hour monitoring.” But now you’ve discovered some egregious vandalism right under one of the cameras. What happened? Was anyone watching that camera? Why didn’t you hear about it? Weren’t you paying for 24-hour coverage?
It’s likely you had a miscommunication with your provider somewhere. The reason is that “monitoring” has many different meanings in the context of alarms and security. It can be easy for sellers and buyers to talk about two different things. There are even stories of unscrupulous sellers exploiting that difference to close sales.
The guide below will help you understand the different types of monitoring, match them to your needs, and outline questions to ask providers or bidders.
Do you need monitoring?
The first question to ask is whether you even need monitoring. Audible alarms and visible cameras often provide strong deterrent effects and provide strong forensic support even without being connected to a monitoring and response system.
If monitoring is required by an insurer, corporate office, regulator, or other stakeholder, make sure you clarify with them which type of monitoring they need (see below). If the goal of your monitoring system is to rapidly detect and respond to security events, consider what types of events you are trying to protect against and then select the cheapest type of monitoring that will recognize those events.
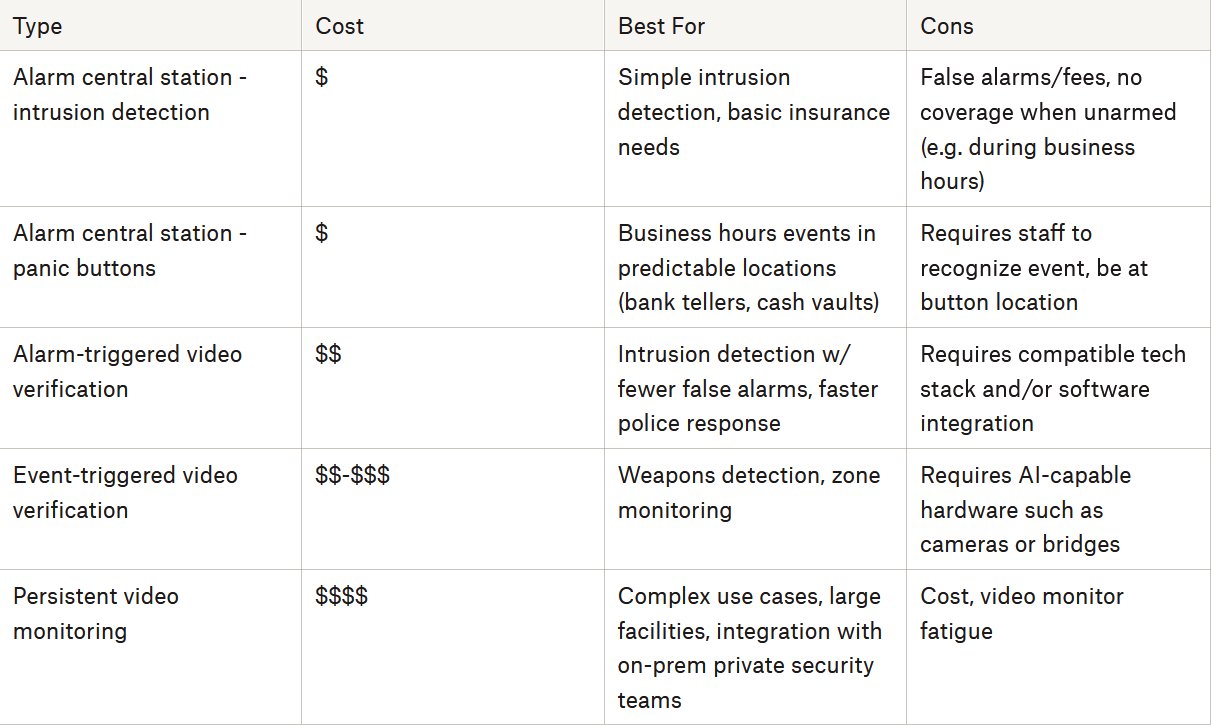
Types of monitoring
Central Station Monitoring
The simplest type of monitoring is central station monitoring of a traditional alarm system. In these systems, an electronic device such as a door contact, glass break detector, motion detector, or panic button sends a simple telephone or LTE cellular signal to a monitoring station. The station will follow simple protocols to confirm the alarm, such as calling the phone number of an account holder. When the alarm is confirmed, the police will be called.
This is a very mature market segment. Once installed, these types of systems are very cheap to monitor. Their biggest downside is that they can generate large numbers of false alarms if not managed carefully. In some jurisdictions or for some types of clients, municipal false alarm fees can quickly become large expenses.
There are also limitations of the system design. Intrusion systems only work when armed, so provide no coverage for events that may happen during working hours. Panic buttons can provide working hour coverage, but require employees to be near the button; they are normally used at specific high-risk workstations like bank tellers or cash vaults.
Alarm-Triggered Video Verification
The next level of monitoring is to add video verification to a central station alarm system. This can help the central station reduce alarm fees by viewing a video feed from the facility before calling the police. If the video does not show any security events in progress, the police will not be called.
In the case that police do need to be called, video verification offers big benefits to police response time. Due to the number of false alarms un-verified systems generate, they are often low on police dispatch priorities. A dispatcher will place a higher priority on an active event that is being monitored by video.
These services may slightly increase costs, but the biggest downside is that cameras, alarm system, and central monitoring station must all be compatible (or use and configure potentially-expensive third-party integration software).
Event-Triggered Video Verification
Cameras and video feeds can also be used to trigger review and response protocols. Using software that analyzes feeds, unexpected video events can route a notification to business users or central stations. These event include motion in unexpected times or places, unexpected types of motion or object counts, or detecting aggressive behavior or weapons.
Identifying these types of events may require specialized hardware and/or software packages, such as specialized cameras or bridge devices that monitor camera feeds. Many modern IP cameras offer basic analytics, but advanced weapon or behavioral detection is often done by advanced AI vendors at an additional fee.
Without relying on alarm hardware, compatibility can be wider between camera and monitoring station, although not all stations work with all types of hardware, so this is still important to get right. Because most monitors in this space specialize, tight integration between video systems and monitoring systems also opens additional response options, such as two-way audio communication between the device and the monitoring station.
The biggest downside to these systems is cost. Most IP cameras are compatible with most software packages thanks to industry standards like ONVIF. Configuring alert zones and times can take extra configuration time. Custom AI training is also feasible, but often requires learning time and advanced skillsets to deploy effectively.
Persistent Video Monitoring
The highest end monitoring option is persistent video monitoring, in which video feeds are monitored by trained personnel regardless of alarm or event status. These video monitoring stations can be remote or onsite. They are regular features in movies and TV shows and are what many buyers imagine when they hear “24/7 monitoring.”
These systems allow for the greatest level of human judgement and review and, when deployed effectively, allow for the fastest and best-coordinated response to security events. Onsite video monitoring stations provide excellent integration with and extension of on-premise private security teams. They are best for complex operations that make exceptions difficult to program into event-triggered systems.
Nonetheless, persistent monitoring is labor-intensive and therefore expensive. Few buyers will need this level of monitoring. Those that do will need to work closely with their provider to design operating protocols that provide coverage, but do not fatigue and bore staff.
Questions to Ask Monitoring Providers
What kind of monitoring do you do? Alarm only? Video verified? Persistent?
Is your station compatible with my systems?
For video:
What times do you monitor?
When is verification triggered?
What are your standard protocols for response? Can I customize them?
For persistent monitoring:
How many screens does each staffer have to monitor?
How do you prevent fatigue and boredom?
If events are being missed, determine whether misses occur due to recognition or response.
If failure to recognize:
Are signals being received by the station? Has the system been tested?
Was there a power or communications outage?
Are monitors fatigued or overloaded?
Do cameras have right capability AND right configuration?
Are they compatible with monitoring station equipment?
If failure to respond:
Have response protocols been well-documented?
Is there a bottleneck?
Are unanticipated events causing confusion?
To Set Up New Monitoring Services
If reading this guide has nudged you toward deploying new monitoring services, please contact us! We’ll help make sure you get the right services and that your full security stack is compatible and configured correctly. Get a free site visit and estimate within our service area!
*Settler Security is not a Texas DPS-licensed alarm monitoring company. Monitoring services are provided by licensed monitoring partners. Ask us which solution is the best complement to your camera installation.